If there’s a computer involved, it needs a password. There’s your computer password, the squiggly line you might use to unlock your phone, the password for your email, the PIN for your bank, social media and the list goes on. You’d probably be surprised how many services, accounts and password you have.
We thought it wise to talk about passwords and security with our customers, the teachers, parents and students who use the uEducateUs system, and hopefully demystify why it’s important to use strong passwords, and keep them secure.
The trade-off
There’s a trade-off between ease of use and security.
-
You can have passwords you can easily remember, but that means they’re easy to guess.
-
You can have complicated passwords, but that means they’re hard to remember.
-
You could use a complicated password you can remember for all your accounts.
Learn if your email address or password was included in a data breach on the Have I Been Pwned website.
It's listed as a resource on the Australian Cyber Security Center website.
Easy versus Hard
Criminals use the same trade-off as you do with your passwords: easy versus hard.
It’s a major undertaking to get into a bank, and the FBI, Australian Federal Police and Interpol come looking for you if you manage to break in.
Similarly, you might have heard about “data breaches” in the news, where criminals break into services and steal data which is then made available in the dark corners of the Internet.
Webber Insurance Australia has a comprehensive list of breaches affecting Australians, including companies like Optus, Facebook and video chat app Zoom.
But in reality, criminals aren’t fussy where the money comes from. And the Internet has made this much simpler.
But criminals are only interested in big fish
What would you do if you received this message?
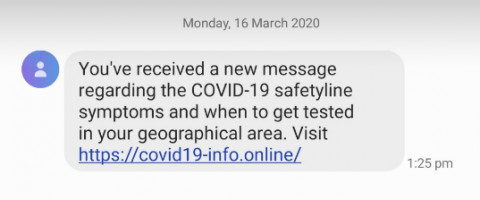
The correct answer is delete this message immediately. It's a criminal scam designed to steal banking details.
This is just one way criminals attempt to get your passwords. The Australian Cyber Security Center website says:
“…one of the most prevalent scams reporting in Australia [is] phishing, a method of stealing confidential information by sending fraudulent messages to a victim…” (our emphasis)
Stolen passwords cost Australians $16 million dollars in 2019 according to the Scamwatch website. They go on to say:
“…Four in 10 Scamwatch reports in 2019 involve attempts to gain information or the actual loss of victims’ information…”
Even if money isn’t stolen, your personal details are gold to criminal organisations across the world. They use them to build legitimate identity documents and get bank loans and buy homes.
Only you’re the one who ends up in debt or a ruined credit rating. Or perhaps it’ll be your children.
Criminals aren’t fussy; to them it’s only a name.
So how do I protect myself and my data?
The Australian government runs several websites to help keep you informed, including:
Scamwatch has this to say about passwords:
“…Choose passwords that would be difficult for others to guess and update them regularly…”
Make sure you avoid the 25 most common passwords found on the Stay Smart Online website which include:
Learn more- password
- 123456
- football
- sunshine
Stay Smart Online recommends the following:
-
First and foremost, use different passwords for each service you use. That way, if one password is exposed, you’ve potentially only lost data in that account, or the use of that password.
-
Second, use passwords that you can’t just remember off the top of your head. This means “Password 1234” is out, and randomly generated characters are in.
-
They also recommend the use of a password manager, which is a like an address book for passwords that only you can get into.
Which password manager should I use?
When choosing a password manager, think about when you’d use it and how. You might only use it at home, or in the office, or when you’re out shopping.
uEducateUs uses Bitwarden to manage passwords across our staff.
There’s a free version for personal use and you can share passwords with one other Bitwarden user account.
Here’s some other welll-known password managers:
We don’t get kickbacks from these companies and you should carefully read their information before starting to use their products. Some involve monthly and annual fees.
One more thing
Some security sites suggest you use “two-factor authentication” and/or “multi-factor authentication”.
They’re slightly different in their behaviour but are a way for you to confirm it’s really YOU who is logging in. You might need to enter a code from your phone or say Yes or No to an SMS or phone notification that pops up. Some banks actually call if they see a possibly fraudulent transaction.
Again, this is a trade-off between ease of use and security. Everything is annoying to use the first few times, but easier with practice.
There’s help available for most services that offer multi-factor authentication and you can Google Search for how to set this up.
For example try entering Facebook multi-factor authentication into Google.
The first result gives instructions how to set it up.
Further Reading
-
Sign up to Have I Been Pwned and get notified if your email address is found in a data breach.
-
Learn more about protecting yourself online on the Stay Smart Online website.
-
Get Smarter With Passwords with the Australian Cyber Security Centre.
-
Sign up to be notified of email and other scams circulating across Australia and the world on the Scamwatch website.
-
Learn how Phone Scams are used to rob people.
-
Read how 10 million Australians were affected in a single data breach.
-
Read more about identity theft.
Terms
There’s a bunch of terms that float around whenever people talk about passwords, so we’ll explain them to make things clearer.
-
Account - An account can take many forms, from the one with your bank, to your uEducateUs account.
-
Characters - individual letters and numbers that may form words, credit cards or other data.
-
Data - information stored in a computer, either your own or on the computers that look after your account for a company. See also “the cloud”.
-
Data Breach - data that is held by a company or organisation that’s been made publicly available, either accidentally or via hacking.
-
Devices - devices with a capital “D” are computers of many different types and sizes, from a big desktop computer, to the smallest smartphone. In many cases, they’re connected to the Internet.
-
Encryption - a mathematical formula that turns data (say a password) into gibberish. They’re kind of like a door lock because you use a key to unlock the data.
-
Exposed - means the data or password has been made public, available to all.
-
Hacker - There are two basic types of “hacker”, the names based on old western movies:
-
White-Hat (the “good guys”) who research computer and internet security;
-
Black-Hat (the “bad guys”) who use their skills without considering the consequences, breaking into anything they can.
-
-
Password - a series of characters when paired with a user name grants access to an Account.
-
Security Breach - similar to a data breach, except it’s the surrounding systems that have been hacked. It’s the difference between your bank’s front door left open overnight (security breach) , or all the money stolen (data breach).
-
User Name - a name for an account which when paired with a password, grants access to an Account.
Here’s some terms that might also be of help:
-
The Cloud - The joke runs “The Cloud isn’t”. The Cloud is a set of internet connected computers that aren’t yours. They tend to be stored in huge warehouses and run websites, banks and every website across the internet.
-
Internet - The Internet actually started in the late 1960s, but has expanded across the world. Think of this as “Inter” like “International”. Computers across a wide area are connected together in a network and most data is publicly available to see
-
Intranet - Think of this as “Intra” as in “Internal”. This is a network of computers connected in say, a business premises.
-
Network - a group of connected computers. The Internet is a massive network of connected computers.
-
Public - open to all without restrictions. For example, news websites.
-
Private - closed unless you have a username and password. For example, your uEducateUs account.
-
World Wide Web - started in the early 1990s, this is what we mostly think of as “The Internet”, but is actually a small proportion of the available information. It’s where the term “website” comes from, and where you actually go when you visit your bank website or connect to Skype or Facebook.